Authenticate users with one-time passwords in Amazon Lex chatbots
Today, many companies use one-time passwords (OTP) to authenticate users. An application asks you for a password to proceed. This password is sent to you via text message to a registered phone number. You enter the password to authenticate. It is an easy and secure approach to verifying user identity. In this blog post, we’ll describe how to integrate the same OTP functionality in an Amazon Lex chatbot.
Amazon Lex lets you easily build life-like conversational interfaces into your existing applications using both voice and text.
Before we jump into the details, let’s take a closer look at OTPs. OTP is usually a sequence of numbers that is valid for only one login session or transaction. The OTP expires after a certain time period, and, after that, a new one has to be generated. It can be used on a variety of channels such as web, mobile, or other devices.
In this blog post, we’ll show how to authenticate your users using an example of a food-ordering chatbot on a mobile device. The Amazon Lex bot will place the order for users only after they have been authenticated by OTP.
Let’s consider the following conversation that uses OTP.
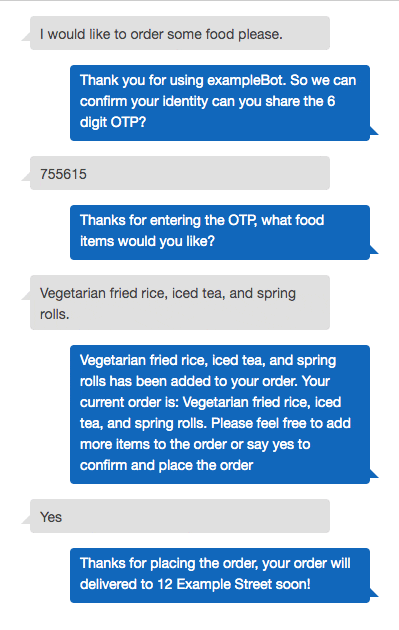
To achieve the interaction we just described, we build a food delivery bot first with the following intents: GetFoodMenu and OrderFood. The OTP password is used in intents that involve transactions, such as OrderFood.
We’ll show you two different implementations of capturing the OTP – one via voice and the other via text. In the first implementation, the OTP is captured directly by Amazon Lex as a voice or text modality. The OTP value is sent to directly to Amazon Lex as a slot value. In the second implementation, the OTP is captured by the client application (using text modality). The client application captures the OTP from the dialog box on the client and sends it to Amazon Lex as a session attribute. Session attributes can be encrypted.
It is important to note that all API calls made to the Amazon Lex runtime are encrypted using HTTPS. The encryption of the OTP when used via session attributes provides an extra level of security. Amazon Lex passes the OTP received via the session attribute or slot value to an AWS Lambda function that can verify the OTP.
Application architecture
The bot has an architecture that is based on the following AWS services:
- Amazon Lex for building the conversational interface.
- AWS Lambda to run data validation and fulfillment.
- Amazon DynamoDB to store and retrieve data.
- Amazon Simple Notification Service (SNS) to publish SMS messages.
- AWS Key Management Service (KMS) to encrypt and decrypt the OTP.
- Amazon Cognito identity pool to obtain temporary AWS credentials to use KMS.
The following diagram illustrates how the various services work together.
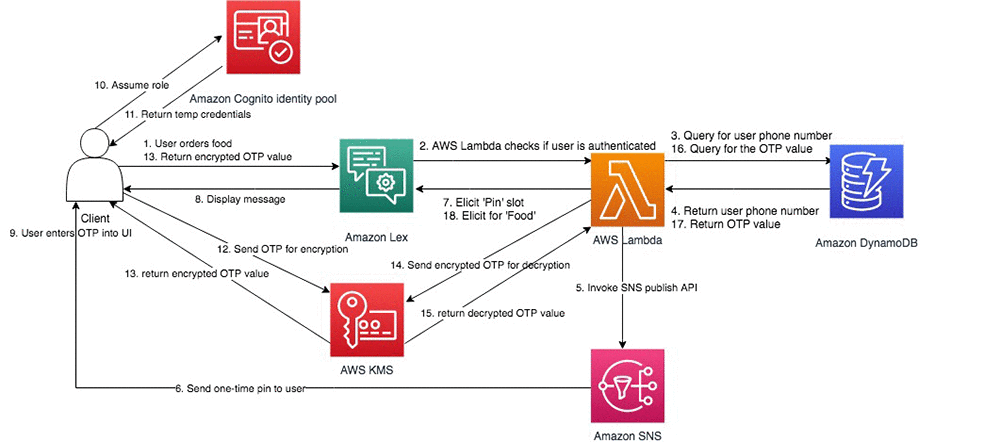
Capturing the OTP using voice modality
When the user first starts an interaction with the bot, the user’s email or other metadata are passed from the frontend to the Amazon Lex runtime.
An AWS Lambda validation code hook is used to perform the following tasks:
- AWS Lambda generates an OTP and stores it in the DynamoDB table.
- AWS Lambda sends the OTP to user’s mobile phone using SNS.
- The user inputs the OTP into the client application, which gets sent as a slot type to Amazon Lex.
- AWS Lambda verifies the OTP, and, if the authentication is successful, it signals Amazon Lex to proceed with the conversation.
After the user is authenticated the user is able to place an order with the Amazon Lex bot.
Capturing the OTP using text modality
Similar to the first implementation, the user’s email or other metadata are sent to the Amazon Lex runtime from the front end.
In the second implementation, an AWS Lambda validation code hook is used to perform the following tasks:
- AWS Lambda generates an OTP and stores it in the DynamoDB table.
- Lambda sends the OTP to user’s mobile phone using SNS.
- User enters the OTP into the dialog box of the client application.
- The client application encrypts the OTP entered by the user and sends it to the Amazon Lex runtime in the session attributes.
Note: Session attributes can be encrypted.
- AWS Lambda verifies the OTP, and, if the authentication is successful, it signals Amazon Lex to proceed with the conversation.
Note: if the OTP is encrypted, the Lambda function will need to decrypt it first.
After the user is authenticated, the user can place an order with the Amazon Lex bot.
Generating an OTP
There are many methods of generating an OTP. In our example, we generate a random six-digit number as an OTP that is valid for one minute and store it in a DynamoDB table. To verify the OTP, we compare the value entered by the user with the value in the DynamoDB table.
Deploying the OTP bot
Use this AWS CloudFormation button to launch the OTP bot in the AWS Region us-east-1:
The source code is available in our GitHub repository.
Open the AWS CloudFormation console, and on the Parameters page, enter a valid phone number. This is the phone number the OTP is sent to.
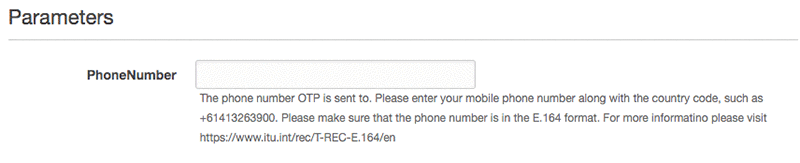
Choose Next twice to display the Review page.
Select the acknowledgement checkbox, and choose Create to deploy the ExampleBot.
The CloudFormation stack creates the following resources in your AWS account:
- Amazon S3 buckets to host the ExampleBot web UIs.
- Amazon Lex Bot to provide natural language processing.
- AWS Lambda functions used to send and validate the OTP.
- AWS IAM roles for the Lambda function.
- Amazon DynamoDB tables to store session data.
- AWS KMS key for encrypting and decrypting data.
- Amazon Cognito identity pool configured to authenticate clients and provide temporary AWS credentials.
When the deployment is complete (after about 15 minutes), the stack Output tab shows the following:
- ExampleBotURL: Click on this URL to interact with ExampleBot.
Let’s create the bot
This blog post builds upon the bot building basics covered in Building Better Bots Using Amazon Lex. Following the guidance from that blog post, we create an Amazon Lex bot with two intents: GetFoodMenu and OrderFood.
The GetFoodMenu intent does not require authentication. The user can ask the bot what food items are on the menu such as:
Please recommend something.
Show me your menu please.
What is on the menu?
What kind of food do you have?
The bot returns a list of food the user can order when the GetFoodMenu intent is elicited.
If the user already knows which food item they want to order, they can order the food item with the following input text to invoke the OrderFood intent:
I would like to order some pasta.
Can I order some food please?
Cheese burger!
Amazon Lex uses the Lambda code hook to check if the user is authenticated. If the user is authenticated, Amazon Lex adds the food item to the user’s current order.
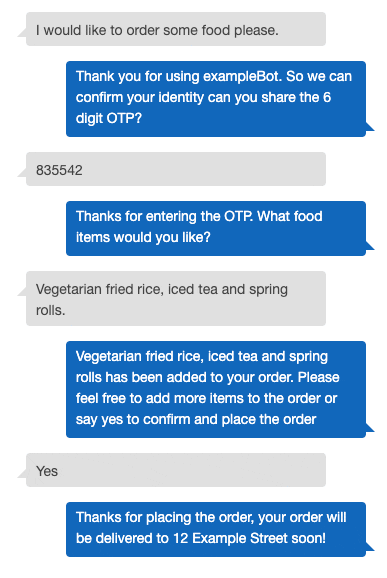
If the user has not been authenticated yet, the interaction looks like this:
User: I would like to order some pasta.
Bot: It seems that you are not authenticated yet. We have sent an OTP to your registered phone number. Please enter the OTP.
User: 812734
Note: If the user is using the text modality, the user’s “to” input can be encrypted.
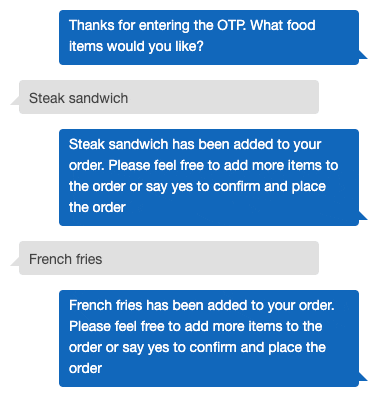
Bot: Thanks for entering the OTP. We’ve added pizza to your order. Would you like anything else?
If the user is not authenticated, Amazon Lex initiates the multifactor authentication (MFA) process. AWS Lambda queries the DynamoDB table for that user’s mobile phone number and delivery address. After DynamoDB returns the values, AWS Lambda generates an OTP based on the metadata of the user, saves it in a DynamoDB table with a UUID as a primary key, and stores it in the session attributes. Then AWS Lambda uses SNS to send an OTP to the user and elicit the pin using the pin slot in the OrderFood intent.
After the user inputs the OTP, Amazon Lex uses the Lambda code hook to validate the pin. AWS Lambda queries the DynamoDB table with the UUID in the session attributes to verify the OTP. If the pin is correct, the Lambda function queries DynamoDB for the secret data; if the pin is incorrect, Lambda performs the validation step again.
Implementation details
The following tables and screenshots show you the different slot types and intents, and how you can use the AWS Management Console to specify the ones you want.
Slots
| Slot type: | Slot Values |
| Food | Amazon.Food |
| Pin | Amazon.Number |
Intents
| Intent Name | Sample Utterances |
| OrderFood |
I would like to order some {Food} {Food} I would like {food} order {food} Can I order some food please Can I order some {Food} please |
| GetFoodMenu |
Please recommend something. Show me your menu, please. What is on the menu? What kind of food do you have? |
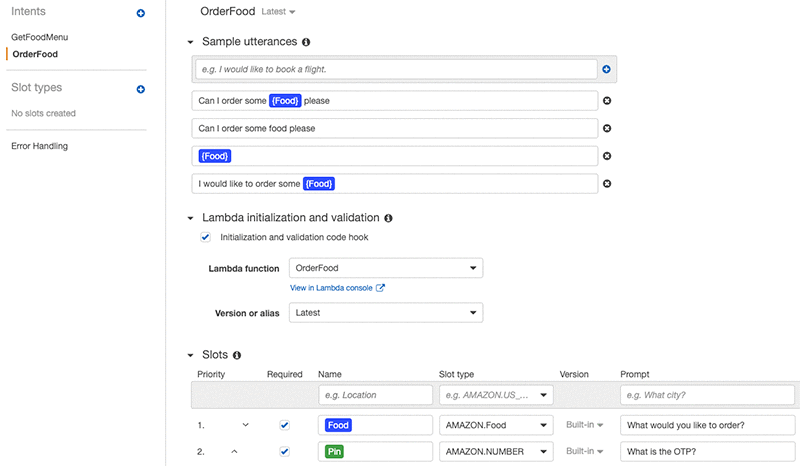
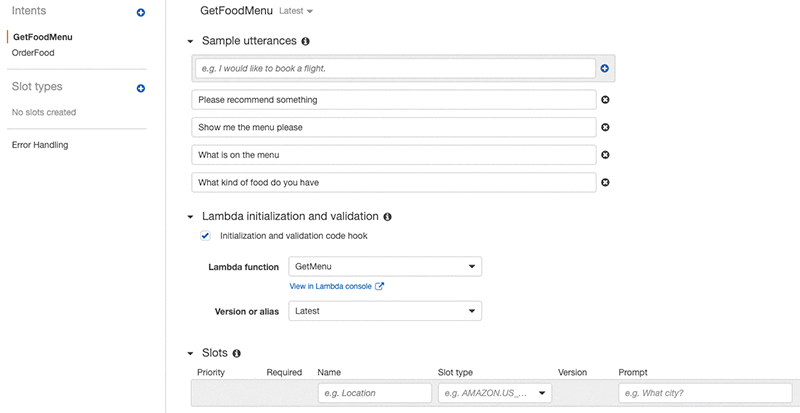
The GetFoodMenu intent uses the GetMenu Lambda function as the initialization and validation code hook to perform the logic, whereas the OrderFood intent uses the OrderFood Lambda function as the initialization and validation code hook to perform the logic.
These are the steps the Lambda function follows:
- The Lambda function first checks which intent the user has invoked.
- If the payload is for the GetFoodMenu intent:
- We’re assuming that the client will send the following items in the session attribute for the first Amazon Lex runtime API call. Since we cannot pass session attributes in the Lex console, for testing purposes, our Lambda function will create the following session attributes if the session attribute is empty.
{’email’ : ‘user@domain.com’, ‘auth’ : ‘false’, ‘uuid’: None, ‘currentOrder’: None, ‘encryptedPin’: None}- ’email’ is the email address of the user.
- ‘auth’ : ‘false’ implies the user is unauthenticated.
- ‘uuid’ is a flag used later as the primary key to store the OTP into the DynamoDB.
- ‘currentOrder’ will keep track of the food items ordered by the user.
- ‘encryptedPin’ will be used by the frontend client to send encrypted OTP. If the implementation does not require OTP to be encrypted, then this attribute is optional.
- The Lambda function will return a list of food items and ask the user which food items they wish to order. In other words, the Lambda function will elicitSlot for the Food slot in the OrderFood
- We’re assuming that the client will send the following items in the session attribute for the first Amazon Lex runtime API call. Since we cannot pass session attributes in the Lex console, for testing purposes, our Lambda function will create the following session attributes if the session attribute is empty.
- If the payload is for the OrderFood intent:
- As we stated earlier, for testing purposes our Lambda function will create the following session attribute if the session attributes are empty.
{’email’ : ‘user@domain.com’, ‘auth’ : ‘false’, ‘uuid’: None, ‘currentOrder’: None, ‘encryptedPin’: None} - If the user is authenticated, the Lambda function will add the requested food item to currentOrder in the session attributes.
- The Lambda function will query the phoneNumbers DynamoDB table using the email for the phone number of the user.
- If DynamoDB is not able to return a phone number matching that email address, the Lambda function will tell the user it wasn’t able to find a phone number associated with that email and will ask the user to contact support.
- The Lambda function will generate an OTP and an uuid. The uuid is stored in the session attributes and the key value pair { uuid : OTP} will be stored as a record in the onetimepin DynamoDB table.
- The Lambda function will use SNS to send the OTP to the user’s phone number and ask the user to enter the one time pin they received by eliciting the pin slot in the OrderFood
- After the user enters the pin, the Lambda function will query the onetimepin DynamoDB table for the record with the uuid stored in the sessionAttributes.
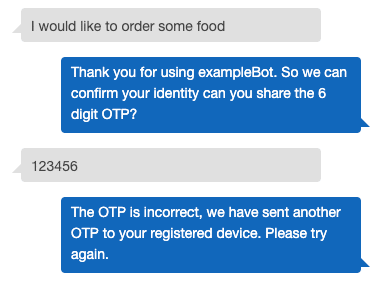
- If the user enters an incorrect pin, the Lambda function will generate a new OTP, store it in DynamoDB, update the uuid in Session Attributes, send this new OTP to the user via SNS again, and ask the user to enter the pin again. The following screenshot illustrates this.

- If the pin is correct Lambda will validate the food item the user is requesting.
- If the “Food” slot type is null, Lambda will ask the user which data they are interested in by eliciting the “Food” slot in the “OrderFood” intent.
- Lambda will add the requested food item to ‘currentOrder’ in session attributes.
- If the user enters an incorrect pin, the Lambda function will generate a new OTP, store it in DynamoDB, update the uuid in Session Attributes, send this new OTP to the user via SNS again, and ask the user to enter the pin again. The following screenshot illustrates this.
- As we stated earlier, for testing purposes our Lambda function will create the following session attribute if the session attributes are empty.
- After the user is authenticated, the subsequent items they want to add to the order will not require authentication as long as the session does not expire.

OTP encryption and decryption
In this section, we’ll show you how to encrypt the OTP from the client side before sending the OTP as a session attribute to Amazon Lex. We’ll also show you how to decrypt the session attribute in the Lambda function.
To encrypt the OTP, the frontend needs to use Amazon Cognito identity pool to assume an unauthenticated role that has the permissions to perform the encrypt action using KMS before sending the OTP through to Amazon Lex as a session attribute. For more information on Amazon Cognito identity pool, see the documentation.
After the Lambda function receives the OTP if it is encrypted Lambda uses KMS to decrypt the OTP and query a Dynamo DB table to confirm if the OTP is correct.
Please refer to the documentation linked here for the prerequisites:
Ensure that unauthenticated identities are enabled.
- Create a KMS key.
- Lock down access to the KMS key to the unauthenticated role created in step 1.
- Allow the unauthenticated Amazon Cognito role to use this KMS to perform the encrypt action.
- Allow the Lambda function’s IAM role the decrypt KMS action.
- Here is an example of the two key policy statements that illustrate this.
Now we are ready to use the frontend to encrypt the OTP:
- In the frontend client, use the GetCredentialsForIdentity API to get the temporary AWS credentials for the unauthenticated Amazon Cognito role. These temporary credentials are used by the frontend to access the AWS KMS service.
- The frontend uses the KMS Encrypt API to encrypt the OTP.
- The encrypted OTP is sent to Amazon Lex in the session attributes.
- The Lambda function uses the KMS Decrypt API to decrypt the encrypted OTP.
- After the OTP is decrypted the Lambda function validates the OTP value.
Conclusion
In this post we showed how to use OTP functionality on an Amazon Lex bot using a simple example. In our design we used AWS Lambda to run data validation and fulfillment; DynamoDB to store and retrieve data; SNS to publish SMS messages; KMS to encrypt and decrypt the OTP; and Amazon Cognito identity pool to obtain temporary AWS credentials to use KMS.
It’s easy to incorporate the OTP functionality described here into any bot. You can pass the OTP pin from the frontend to Amazon Lex either as a slot value or session attribute value in your intent. Then, send and perform the validation using a Lambda function, and your bot is ready to accept OTP!
About the Author
 Kun Qian is is a Cloud Support Engineer at AWS. He enjoys providing technical guidance to customers, and helping them troubleshoot and design solutions on AWS.
Kun Qian is is a Cloud Support Engineer at AWS. He enjoys providing technical guidance to customers, and helping them troubleshoot and design solutions on AWS.
Tags: Archive

Leave a Reply