Securing Amazon SageMaker Studio connectivity using a private VPC
Amazon SageMaker Studio is the first fully integrated development environment (IDE) for machine learning (ML). With a single click, data scientists and developers can quickly spin up Amazon SageMaker Studio Notebooks for exploring datasets and building models. With the new ability to launch Amazon SageMaker Studio in your Amazon Virtual Private Cloud (Amazon VPC), you can control the data flow from your Amazon SageMaker Studio notebooks. This allows you to restrict internet access, monitor and inspect traffic using standard AWS networking and security capabilities, and connect to other AWS resources through AWS PrivateLink or VPC endpoints.
In this post, we explore how the Amazon SageMaker Studio VPC connectivity works, implement a sample architecture, and demonstrate some security controls in action.
Solution overview
When experimenting with and deploying ML workflows, you need access to multiple resources, such as libraries, packages, and datasets. If you’re in a highly regulated industry, controlling access to these resources is a paramount requirement. Amazon SageMaker Studio allows you to implement security in depth, with features such as data encryption, AWS Identity and Access Management (IAM), and AWS Single Sign-On (AWS SSO) integration. The ability to launch Amazon SageMaker Studio in your own private VPC adds another layer of security.
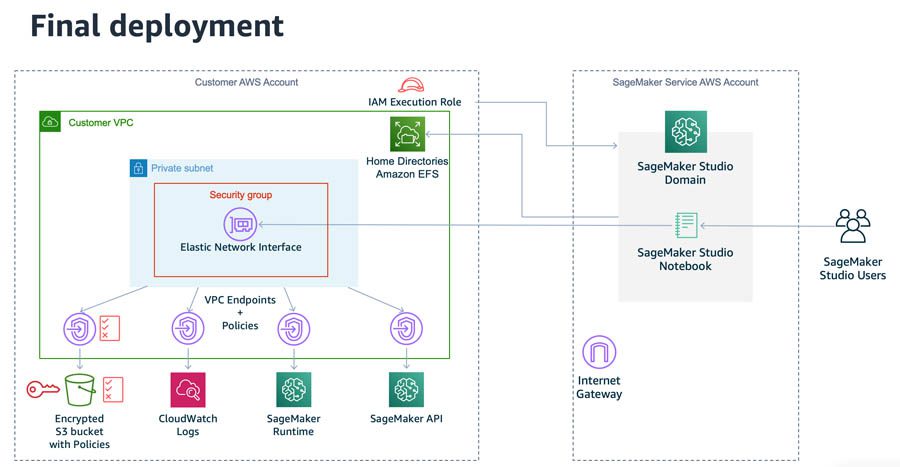
Amazon SageMaker Studio runs on an environment managed by AWS. When launching a new Studio domain, the parameter AppNetworkAccessType defines the external connectivity for such domain. Previously, the only option available for this parameter was DirectInternetOnly, meaning the traffic from the notebook flowed from an AWS managed internet gateway, as described in the following diagram.
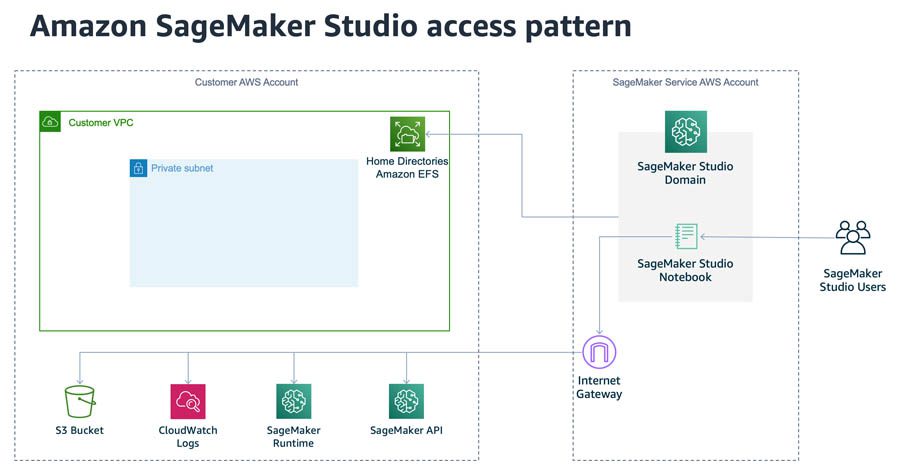
The Amazon Elastic File System (Amazon EFS) volumes that store the Studio users’ home directories resides in the customer VPC, even when AppNetworkAccessType=DirectInternetOnly. You can optionally specify which VPC and subnet to use.
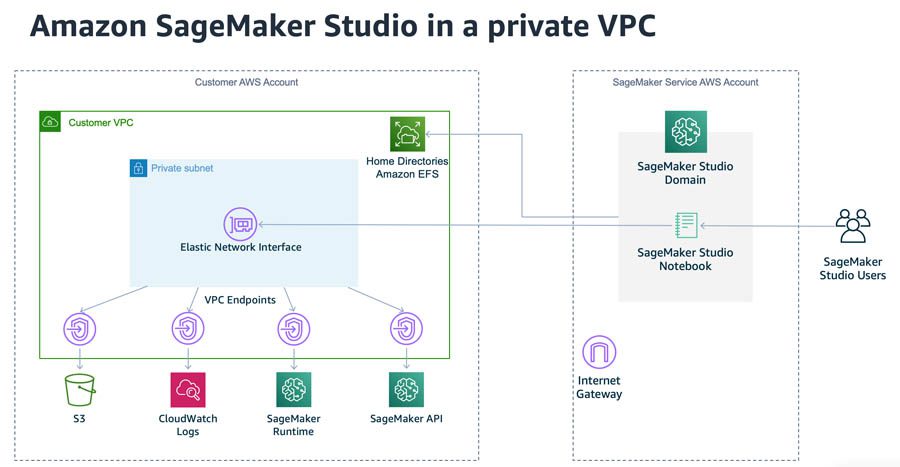
With the newly introduced feature to launch Studio in your VPC, you can set the AppNetworkAccessType parameter to VpcOnly. This launches Studio inside the specified VPC, communicating with the domain through an elastic network interface (ENI). You can apply security groups to that ENI to enforce a first layer of security control.
You can also use VPC endpoints to establish a private connection between the Studio domain and other AWS services, such as Amazon Simple Storage Service (Amazon S3) for data storage and Amazon CloudWatch for logging and monitoring, without requiring internet connectivity. VPC endpoints can impose additional networking controls such as VPC endpoint IAM policies that may, for example, only allow traffic to certain S3 buckets. The following diagram illustrates this architecture.
Prerequisites
Before getting started, make sure you have the following prerequisites:
- An AWS account
- An IAM user or role with administrative access
- Curiosity

Setting up your environment
To better understand how the feature works, we provide an AWS CloudFormation template to set up a basic environment where you can experiment with Amazon SageMaker Studio running inside a VPC. After deployment, the environment looks like the following diagram.
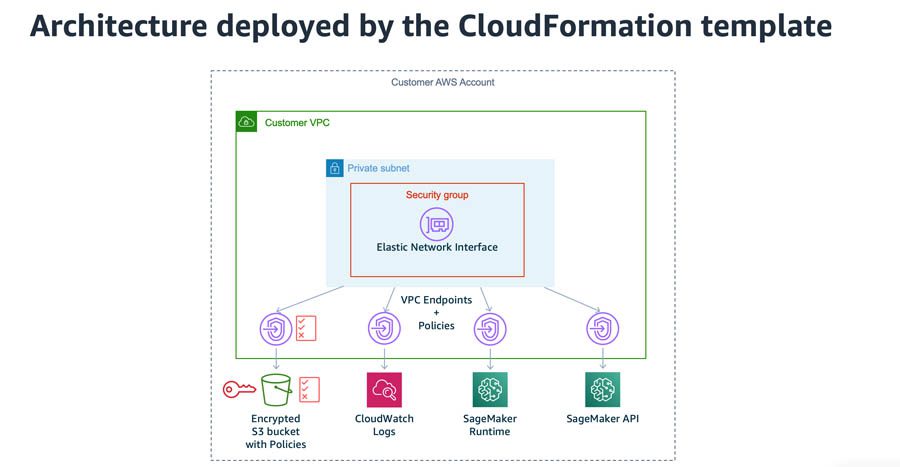
This template deploys the following resources in your account:
- A new VPC, with a private subnet and security group. Because communication occurs across multiple Studio resources, this security group applied to the Studio ENI should allow inbound traffic to itself.
- An encrypted S3 bucket, with bucket policies restricting access to our S3 endpoint.
- VPC endpoints with policies for access control:
- We use an Amazon S3 endpoint to demonstrate the ability to limit traffic to specific S3 buckets.
- Because Studio has its traffic routed through the VPC, access to supporting services needs to be provisioned through VPC endpoints. Amazon CloudWatch Logs allows Studio to push logs generated by the service. We need an Amazon SageMaker API endpoint to launch Studio notebooks, training jobs, processing jobs, and deploy endpoints, and an Amazon SageMaker RunTime endpoint for services to call the Amazon SageMaker inference endpoint.
- An IAM execution role. This role is assigned to Amazon SageMaker and defines which access permissions Studio has.
To set up your environment, click on the link below. The template is also available at this GitHub repo.
Creating an Amazon SageMaker Studio domain inside a VPC
With the infrastructure in place, you’re ready to create an Amazon SageMaker Studio domain and assign it to a VPC.
For more information about the options available to set up Studio, see Onboard to Amazon SageMaker Studio. If you have an existing domain, you might want to delete it and recreate it, or create a separate one.
To create the domain, you can use the following:
- The AWS Command Line Interface (AWS CLI). For instructions, see create-domain.
- The AWS SDK. For instructions, see CreateDomain.
- The AWS Management Console.
To use the console to create a Studio domain and tie it to the VPC infrastructure deployed by the template, complete the following steps:
- On the Amazon SageMaker console, choose SageMaker Studio.
If you don’t have a domain created, a screen appears.
- For Get Started, select Standard setup.
- For Authentication method, select AWS Identity and Access Management (IAM).
- For Execution role for all users, choose your notebook IAM role (the default is
studiovpc-notebook-role). - In the Network section, for VPC, choose your VPC (the default is
studiovpc-vpc). - For Subnet, choose your subnet (the default is
studiovpc-private-subnet).
Make sure to not choose studiovpc-endpoint-private-subnet.
- For Network Access for Studio, select VPC Only.
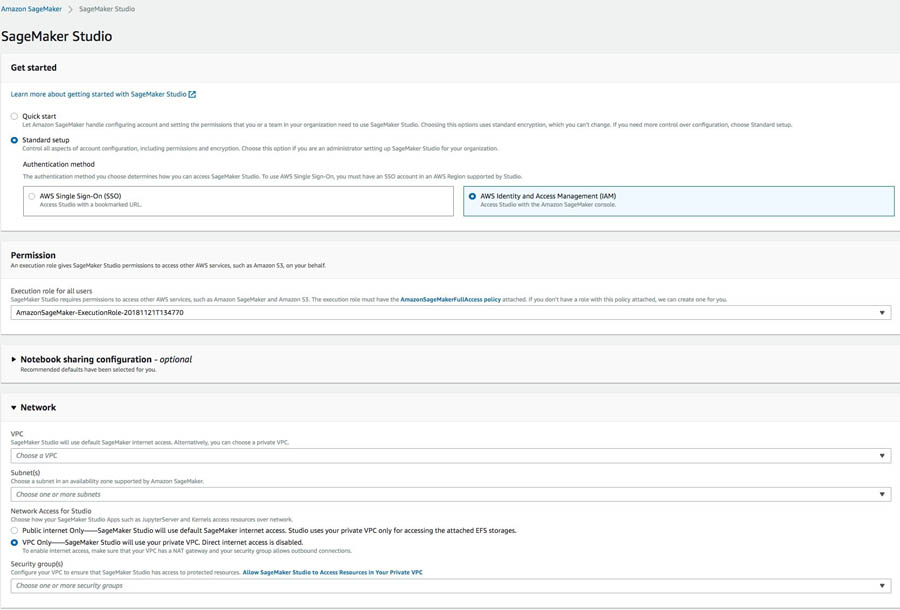
- Choose Submit.
To create and link the domain with the AWS CLI, enter the following code. The option --app-network-access-type VpcOnly links the domain to our VPC. The VPC and subnet parameters are set by the --default-user-settings option.
Creating a user profile
Now that the domain is created, we need to create a user profile. You can create multiple user profiles associated to a single domain.
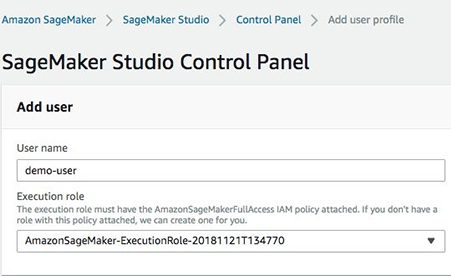
To create your user profile on the console, complete the following steps:
- On the Amazon SageMaker Studio console, choose Control Panel.
- Choose Add user profile.
- For User name, enter a name (for example,
demo-user). - For Execution role, choose your IAM role (the default is
studiovpc-notebook-role).
To create your user profile with the AWS CLI, enter the following code:
Accessing Amazon SageMaker Studio
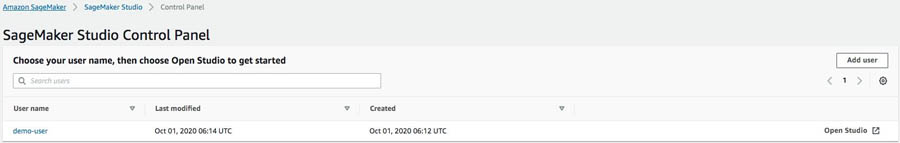
We now have a Studio domain associated to our VPC and a user profile in this domain. Now we need to give access to the user. To do so, we create a pre-signed URL.
To use the console, on the Studio Control Panel, locate your user name and choose Open Studio.
To use the AWS CLI, enter the following code:
At this point, our deployment looks like the following diagram.
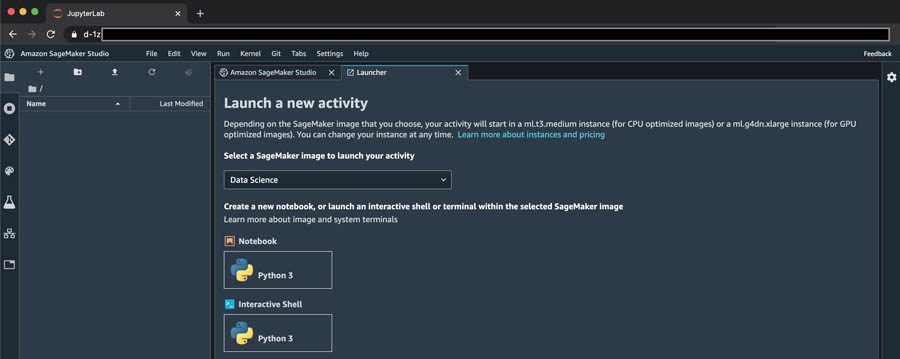
We made it! Now you can use your browser to connect to the Amazon SageMaker Studio domain. After a few minutes, Studio finishes creating your environment and you’re greeted with the launcher screen (see the following screenshot).
Security controls
Some examples of security best practices are Amazon S3 access control and limiting internet ingress and egress. In this section, we see how to implement them in combination with running Amazon SageMaker Studio in a private VPC.
Amazon S3 access control
Developing ML models requires access to sensitive data stored on specific S3 buckets. You might want to implement controls to guarantee that:
- Only specific Studio domains can access these buckets
- Each Studio domain only have access to the defined S3 buckets
We can achieve this using the sample architecture provided in the CloudFormation template.
Our CloudFormation template created an S3 bucket with the following S3 bucket policy attached to it. The condition StringsNotEquals evaluates the VPC endpoint ID with the effect set to deny, meaning that access to the S3 bucket is denied if the access doesn’t come from the designated VPC endpoint. You can find your specific bucket name on the AWS CloudFormation console, on the Outputs tab for the stack.
The Amazon S3 VPC endpoint also has a policy attached to it. This policy only allows access to the S3 bucket created by AWS CloudFormation:
This combination of S3 bucket policy and VPC endpoint policy, together with Studio VPC connectivity, establishes that Studio can only access the referenced S3 bucket, and this S3 bucket can only be accessed from the VPC endpoint.
To test it, open a notebook in Studio and try to copy a file into your S3 bucket. The following screenshot shows that it works as expected.
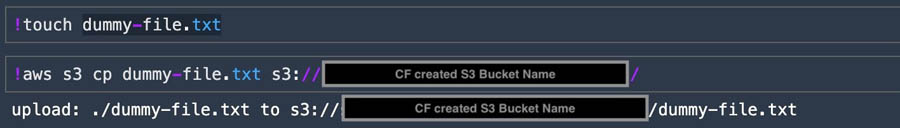
If you try the same with a different S3 bucket, you should get a permission denied error.
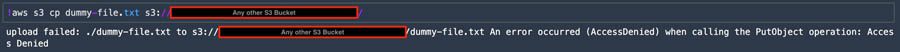
If you try to access the bucket from outside Studio, you should also get a permission error.
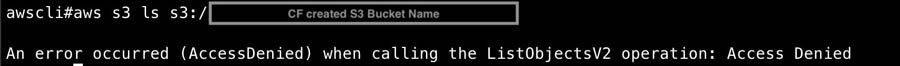
Limiting internet ingress and egress
To develop ML models, data scientists often need access to public code repos or Python packages (for example, from PyPI) to explore data and train models. If you need to restrict access to only approved datasets and libraries, you need to restrict internet access. In our sample architecture, we achieve this by using a private subnet on our VPC, without an internet gateway or NAT gateway deployed.
We can test this by trying to clone a public repository containing Amazon SageMaker example notebooks.
In your Studio environment, open a notebook and enter the following code:
You can also run it in your notebook directly.
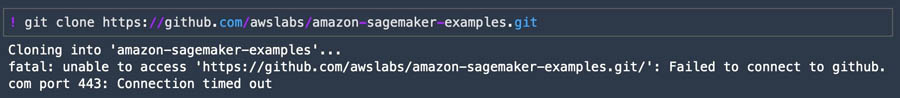
As expected, the connection times out.
If you want to provide internet access through your VPC, just add an internet gateway and the proper routing entries. The internet traffic flows through your VPC, and you can implement other security controls such as inline inspections with a firewall or internet proxy. For more information, see Understanding Amazon SageMaker notebook instance networking configurations and advanced routing options.
Cleaning up
To avoid incurring future charges, delete the resources you created:
- Shut down the notebooks you started with Studio.
- If desired, delete the Studio domain.
- On the AWS CloudFormation console, delete the CloudFormation stack.
Conclusion
You can use Amazon SageMaker Studio to streamline developing, experimenting with, training, and deploying ML models. With the new ability to launch Studio inside a VPC, regulated industries such as financial services, healthcare, and others with strict security requirements can use Studio while meeting their enterprise security needs.
Go test this new feature and let us know what you think. For more information about Amazon SageMaker security, see the following:
- Secure deployment of Amazon SageMaker resources
- Amazon SageMaker Workshop: Building Secure Environments
About the Authors

Rafael Suguiura is a Principal Solutions Architect at Amazon Web Services. He guides some of the world’s largest financial services companies in their cloud journey. When the weather is nice, he enjoys cycling and finding new hiking trails— and when it’s not, he catches up with sci-fi books, TV series, and video games.
 Stefan Natu is a Sr. Machine Learning Specialist at Amazon Web Services. He is focused on helping financial services customers build end-to-end machine learning solutions on AWS. In his spare time, he enjoys reading machine learning blogs, playing the guitar, and exploring the food scene in New York City.
Stefan Natu is a Sr. Machine Learning Specialist at Amazon Web Services. He is focused on helping financial services customers build end-to-end machine learning solutions on AWS. In his spare time, he enjoys reading machine learning blogs, playing the guitar, and exploring the food scene in New York City.
 Han Zhang is a Software Development Engineer at Amazon Web Services. She is part of the launch team for Amazon SageMaker Notebooks and Amazon SageMaker Studio, and has been focusing on building secure machine learning environments for customers. In her spare time, she enjoys hiking and skiing in the Pacific Northwest.
Han Zhang is a Software Development Engineer at Amazon Web Services. She is part of the launch team for Amazon SageMaker Notebooks and Amazon SageMaker Studio, and has been focusing on building secure machine learning environments for customers. In her spare time, she enjoys hiking and skiing in the Pacific Northwest.
Tags: Archive


Leave a Reply