Onboard OneLogin SSO users to Amazon SageMaker Studio
Amazon SageMaker is a fully managed service that provides every machine learning (ML) developer and data scientist the ability to build, train, and deploy ML models at scale. Amazon SageMaker Studio is a web-based, integrated development environment (IDE) for ML. Amazon SageMaker Studio provides all the tools you need to take your models from experimentation to production while boosting your productivity. You can write code, track experiments, visualize data, and perform debugging and monitoring within a single, integrated visual interface.
OneLogin is an identity platform for secure, scalable, and smart experiences that connects people to technology. OneLogin’s authentication and role-based user provisioning engine enables organizations to implement least privilege access controls and eliminate manual user management workflows for all AWS users and accounts.
In this post, we walk you through the steps to onboard existing users in OneLogin to Amazon SageMaker Studio. We also demonstrate the single sign-on (SSO) experience for system administrators and Amazon SageMaker Studio users.
Key Components
The solution contains the following key components:
- AWS SSO – AWS Single Sign-On (AWS SSO) allows you to efficiently manage user identities at scale by establishing a single identity and access strategy across your own applications, third-party applications (SaaS), and AWS environments.
- OneLogin’s connector for AWS SSO – The connector configures SAML 2.0 and System for Cross-domain Integration Management (SCIM) integration between OneLogin and AWS SSO.
- Users and groups – Individual users or users belonging to specific groups like administrators, developers, or finance in OneLogin are automatically synced with AWS SSO via SCIM.
- Domain – A primary component of Amazon SageMaker Studio is a domain. The domain consists of a list of authorized users (called user profiles), and configurations such as Amazon Virtual Private Cloud (Amazon VPC) configurations and the default AWS Identity and Access Management (IAM) execution role.
- User profile – The user profile (user) is a configuration for the user that exists in the SageMaker domain. The user profile defines various configuration settings for the user, including the execution role and the default app specifications.
- Execution role – The IAM execution role is the primary role that is assumed by the users and the service on behalf of the user to allow them to perform certain actions and provision resources in Studio.
Reference Architecture
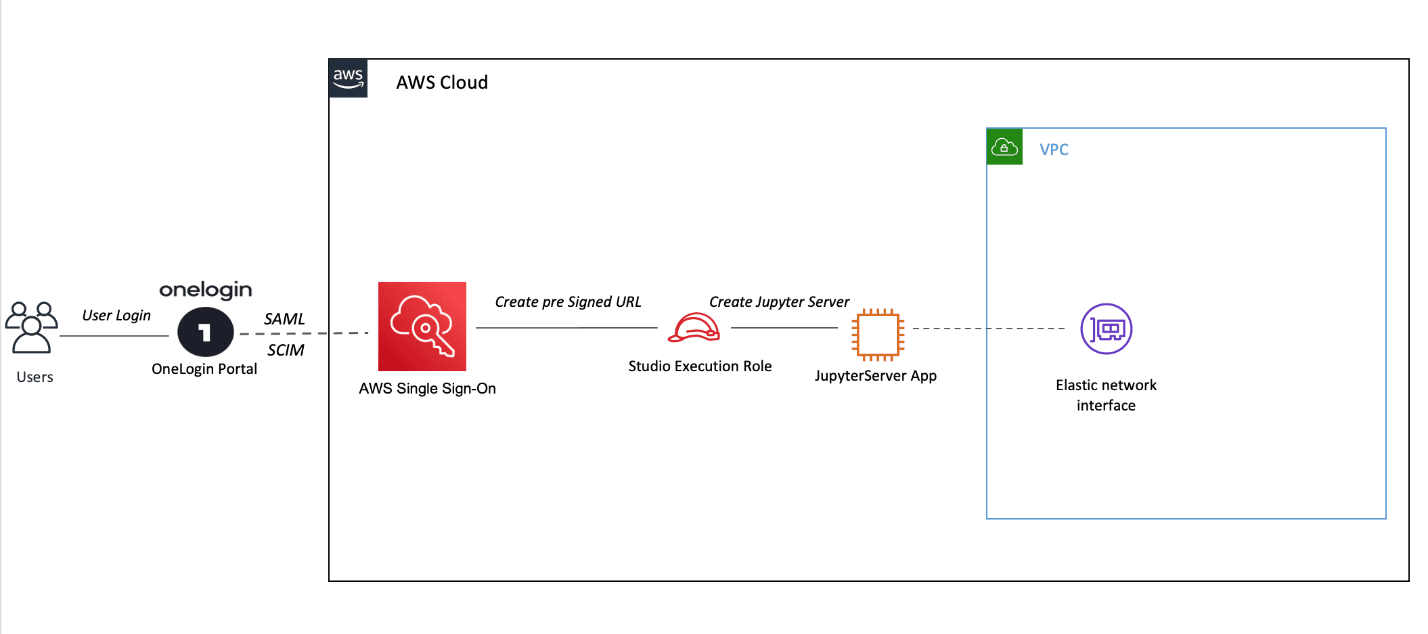
The following architecture diagram shows the flow of authentication and authorization from OneLogin to Amazon SageMaker Studio. Users log in through OneLogin, which authenticates them and passes a SAML authentication to AWS SSO. Once logged in, they can select the Amazon SageMaker Studio app, which assumes the SageMaker execution role attached to their user profile to create a pre-signed domain URL. This pre-signed domain URL is used directly log in the users to their JupyterServer environment.
Prerequisites
Make sure you have the following prerequisites:
- A OneLogin account, for which we use a free OneLogin developer account to create our OneLogin instance and test users
- An AWS account with administrator privileges to set up the AWS SSO integration and access to create policies for Amazon SageMaker Studio
Step 1: Set up the AWS application in OneLogin
On your OneLogin account, log in with administrator privileges and navigate to Applications. In the upper-right, choose Add app. Next, search for and then choose AWS Single Sign-On.
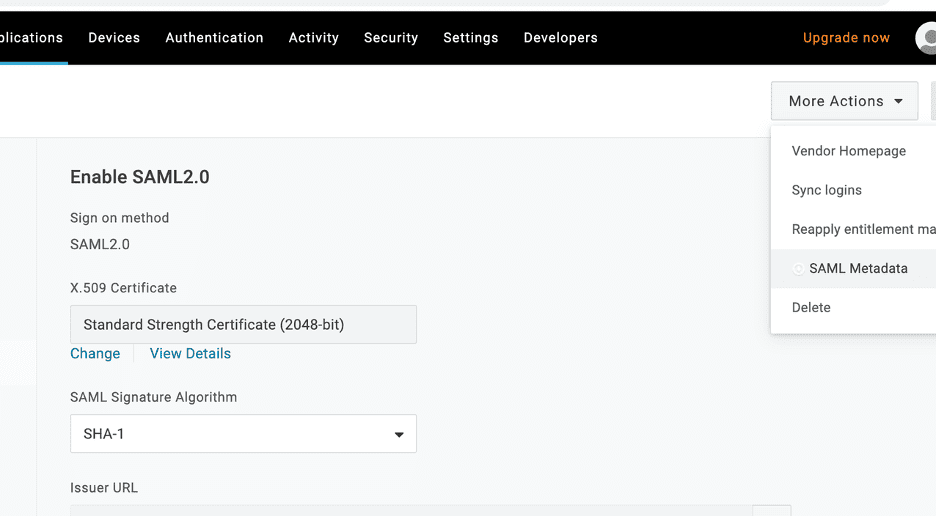
Step 2: Download the Identity Provider Metadata
Next, we need to get the IdP metadata from OneLogin, which we use to register on AWS. Inside your OneLogin AWS Single Sign-On application, navigate to More Actions, then download and save the IdP metadata as onelogin-aws.xml.
Step 3: Enable AWS SSO and set up SCIM
Make sure that AWS SSO is enabled. If not, see Enable AWS SSO. AWS SSO provides support for the SCIM v2.0 standard. SCIM keeps your AWS SSO identities in sync with identities from your IdP. This includes any provisioning, updates, and de-provisioning of users between your IdP and AWS SSO. Using SCIM integration saves your IT and admin teams the time and effort of implementing custom solutions to cross-replicate user names and email addresses between AWS SSO and your IdPs.
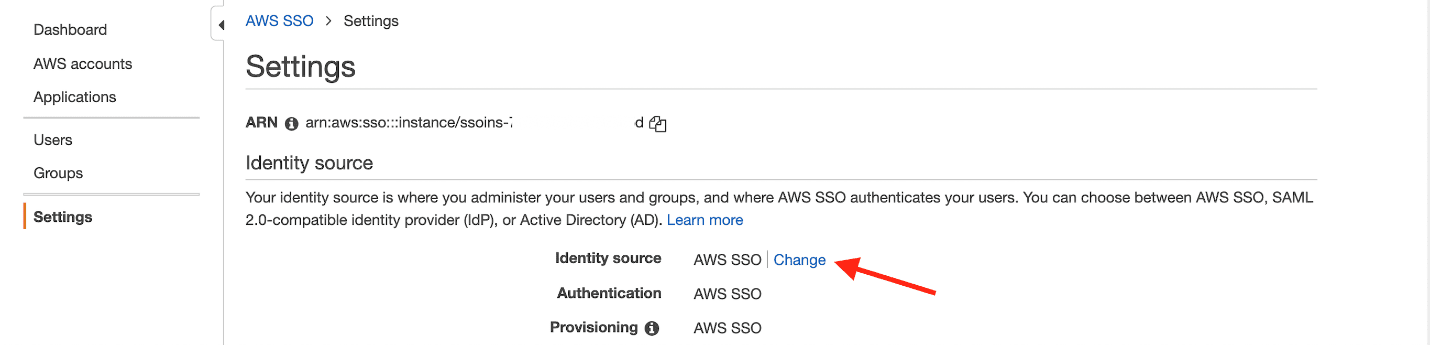
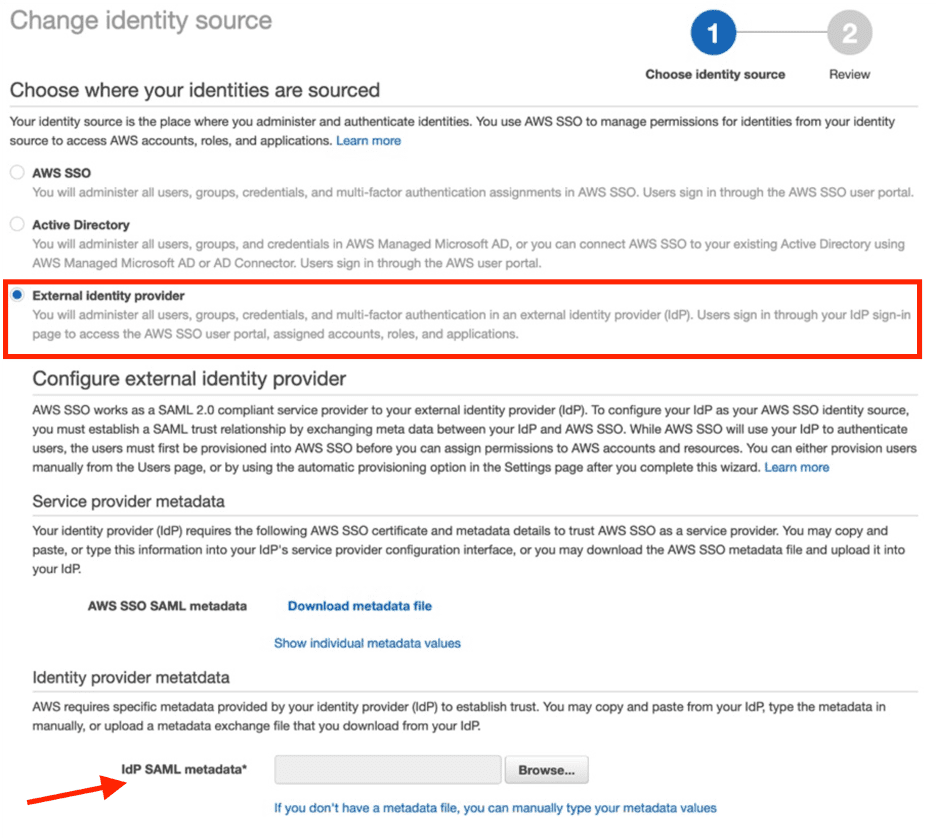
- On the AWS SSO console, choose Settings in the navigation pane.
- Next to Identity source, choose Change.

- Select External identity provider.
- For AWS SSO SAML metadata, upload the OneLogin metadata XML that you downloaded earlier.

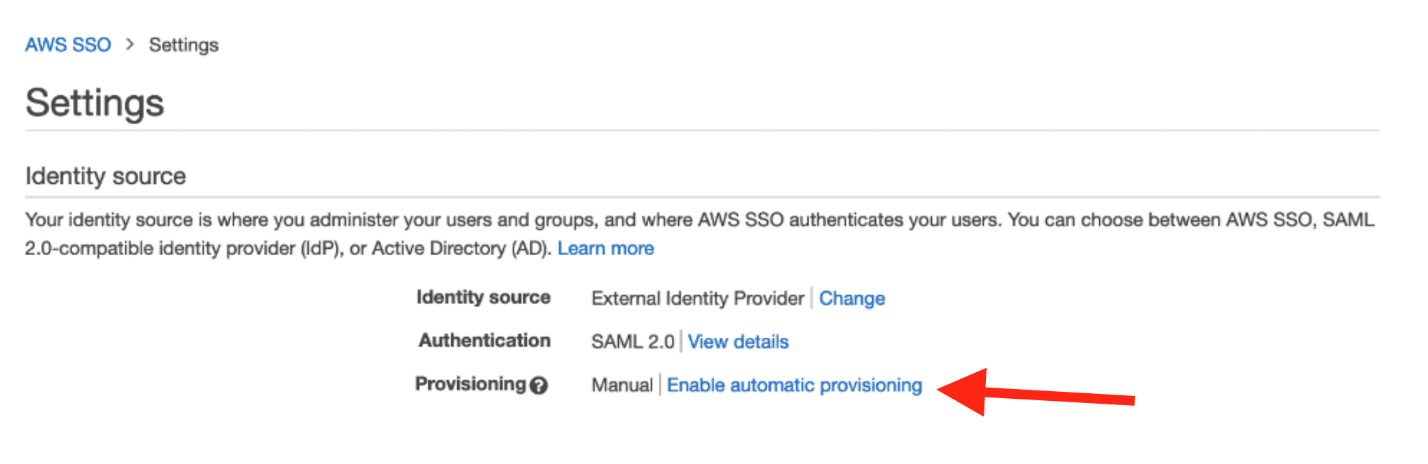
- Update the provisioning from Manual to SCIM by choosing Enable automatic provisioning.

Step 4: Get integration information from AWS SSO
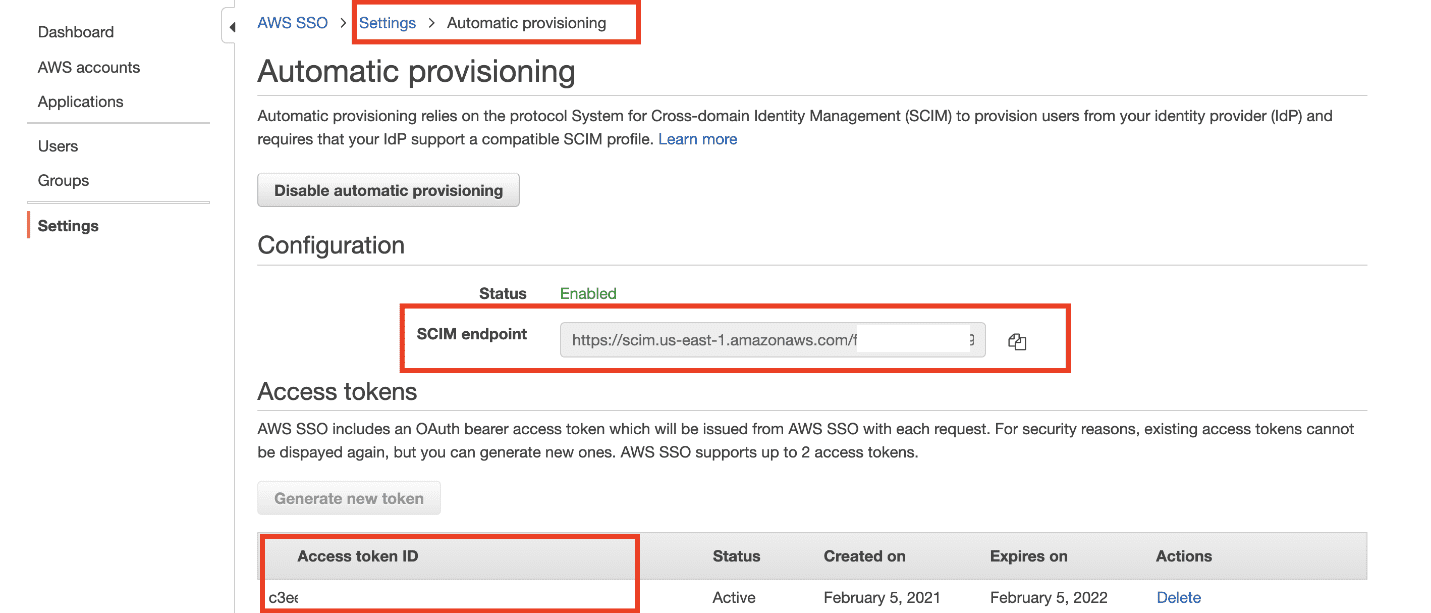
To complete the integration on the OneLogin side, you need the following:
- SCIM endpoint (also known as the SCIM Base URL)
- Access token (also known as a SCIM Bearer token)
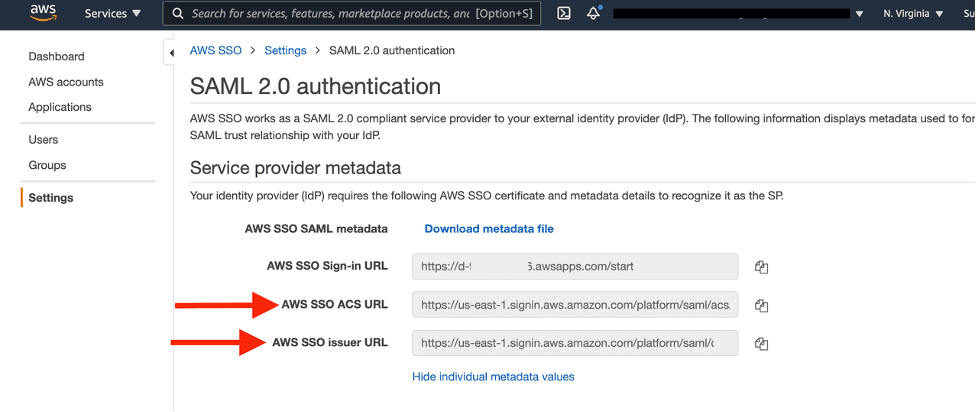
- AWS SSO ACS URL
- AWS SSO issuer URL
The information is available on the Settings page on the AWS SSO console. The endpoint and access token are on the Automatic provisioning page, as shown in the following screenshot.
Choose View details for Authentication SAML 2.0 and copy the AWS SSO ACS URL and AWS SSO issuer URL.
Now that you have these four pieces of information, it’s time to go to OneLogin to finalize the integration.
Step 5: Establish SAML authentication between OneLogin (your IdP) and AWS SSO
To establish your SAML authentication, complete the following steps:
- Log back in to your OneLogin portal as admin into your previously configured AWS SSO app.
- Choose Configuration and enter the details that you gathered in the previous section (AWS SSO issuer URL, AWS SSO ACS URL, SCIM Base URL, and SCIM Bearer token) and choose Save.
Make sure to remove any trailing slashes (/).
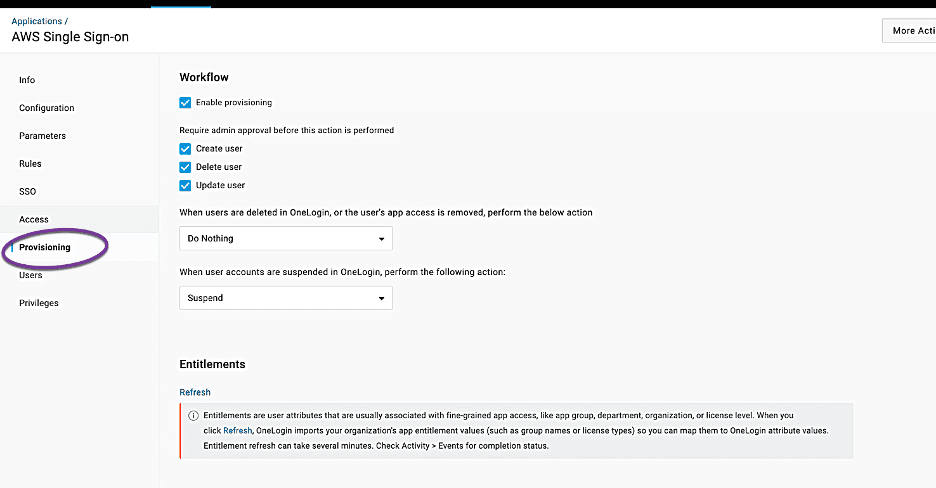
- Choose Provisioning in the navigation pane.
- Select Enable provisioning.
- You can select Create user, Delete user, and Update user for admin approval on these actions.
- Save your configuration.
Step 6: Assign and sync users from OneLogin to AWS SSO, to access Amazon SageMaker Studio
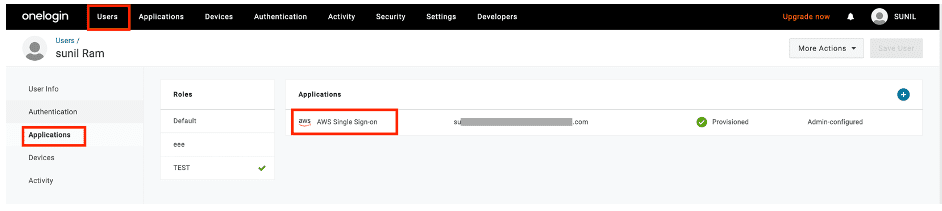
In your OneLogin portal, on the top ribbon navigate to Users and assign the users in your organization to your newly created AWS Single Sign-On application to provide access to Amazon SageMaker Studio.
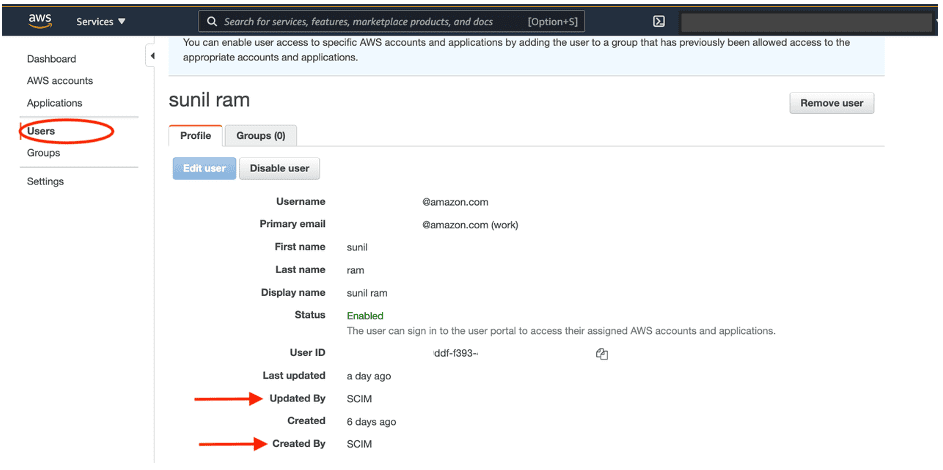
Verify if this user or group has synced into AWS SSO via SCIM by checking the Users page on the AWS SSO console.
Step 7: Create your Amazon SageMaker Studio environment
You can set up your Amazon SageMaker Studio environment by navigating to Amazon SageMaker Studio on your AWS account.
- On the SageMaker console, choose Amazon SageMaker Studio.
- Choose Get started and select Standard setup.
- For Authentication method, select AWS Single Sign-On (SSO).
Make sure that AWS SSO is enabled in the same Region as your Amazon SageMaker Studio.
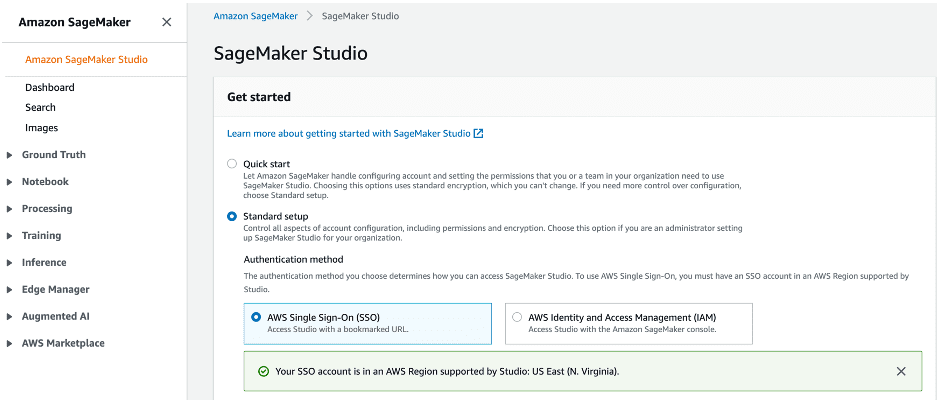
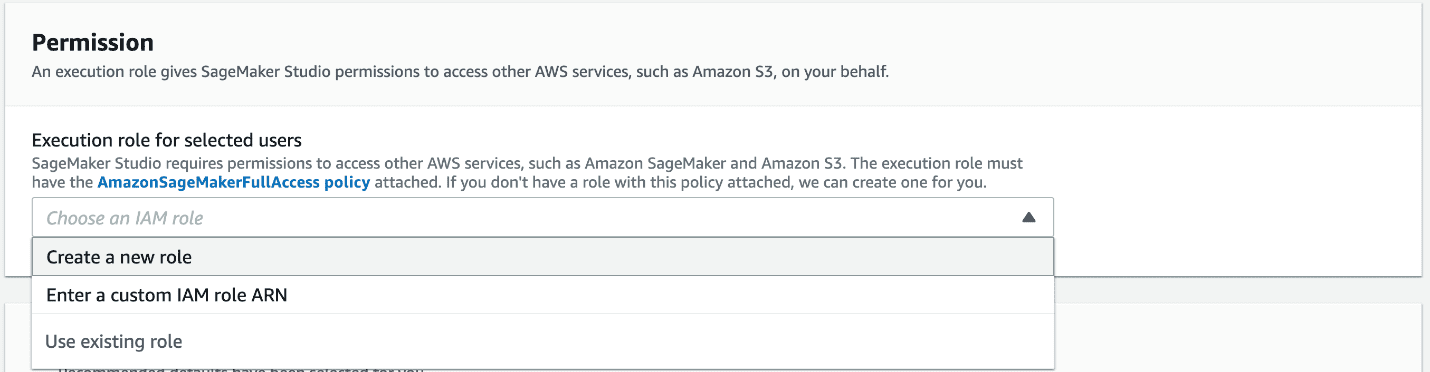
- Under Permission, create a new IAM role with appropriate access to Amazon Simple Storage Service (Amazon S3) buckets, or choose an existing IAM role.

Step 8: Specify additional configurations for Amazon SageMaker Studio
You also have the option to set additional configurations.
- Use the default values for Network sharing configuration and SageMaker Projects and JumpStart.

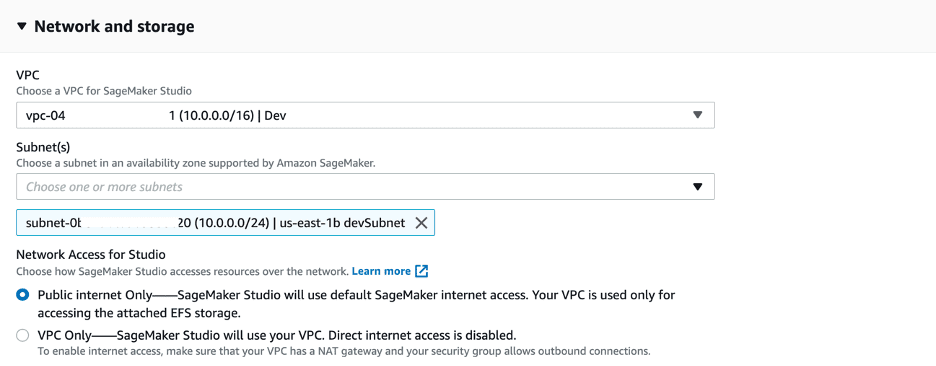
- In the Network and storage section, we use our custom VPC and subnets, which creates the Amazon Elastic File System (Amazon EFS) domain in the VPC we specify.
- Select Public internet Only to allow default internet access for SageMaker.

- Choose Submit.
Amazon SageMaker Studio creates a domain and sets up AWS SSO for the domain. This process should take around 10 minutes to complete. The domain status shows as Ready when the provisioning is complete.
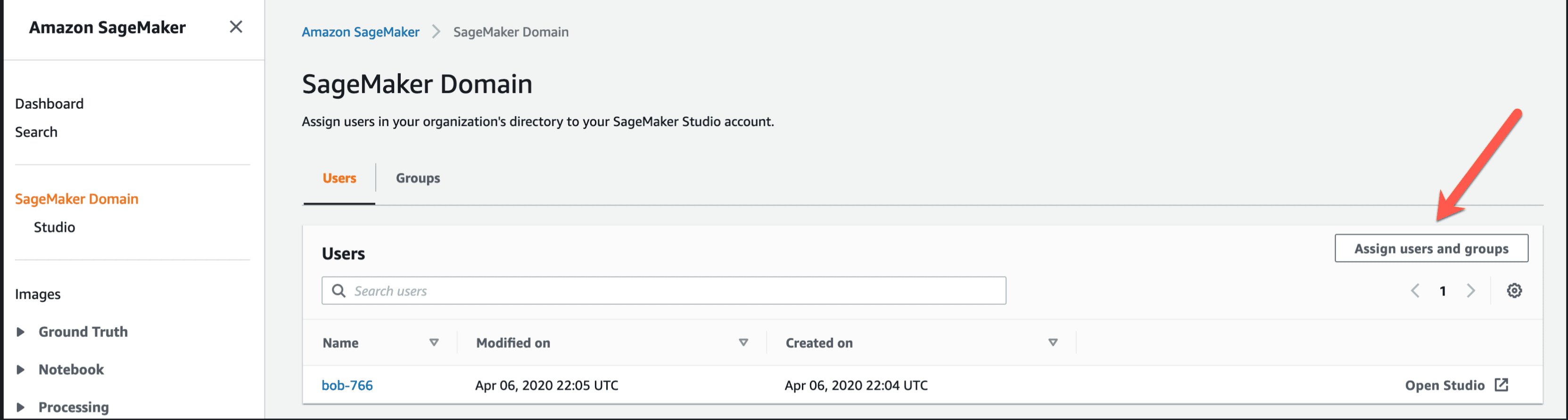
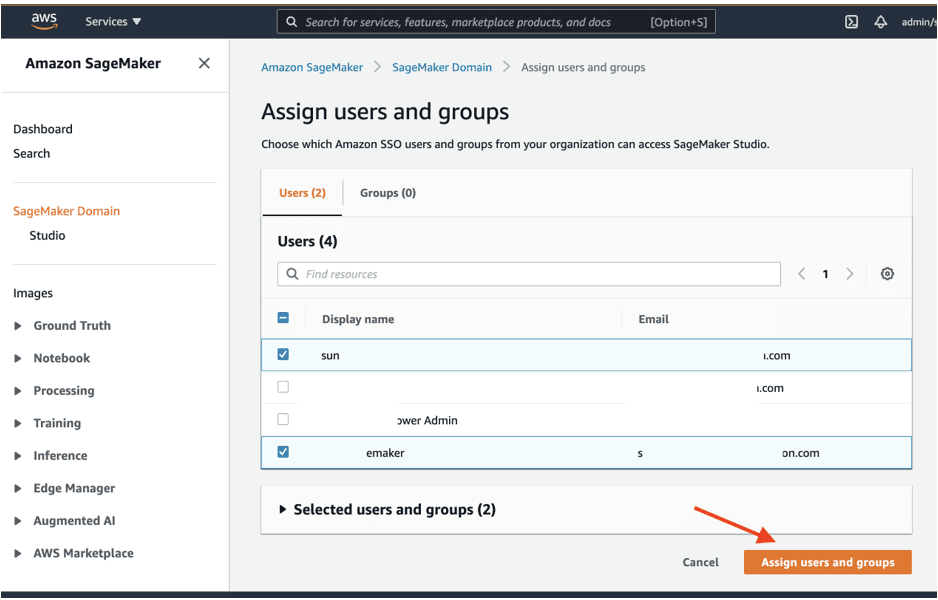
Step 9: Assign users to your newly created Amazon SageMaker Studio Environment
Choose Assign Users and groups to assign users who were created via OneLogin and are synced into AWS SSO.
You can assign users to Amazon SageMaker Studio environment by selecting the check box next to Display name and Email.
Step 10: Verify the integration and log in to your Amazon SageMaker Studio environment
Under Studio Summary, you can notice the Execution Role that you created in the previous step. You can now log in to your Amazon SageMaker Studio environment.
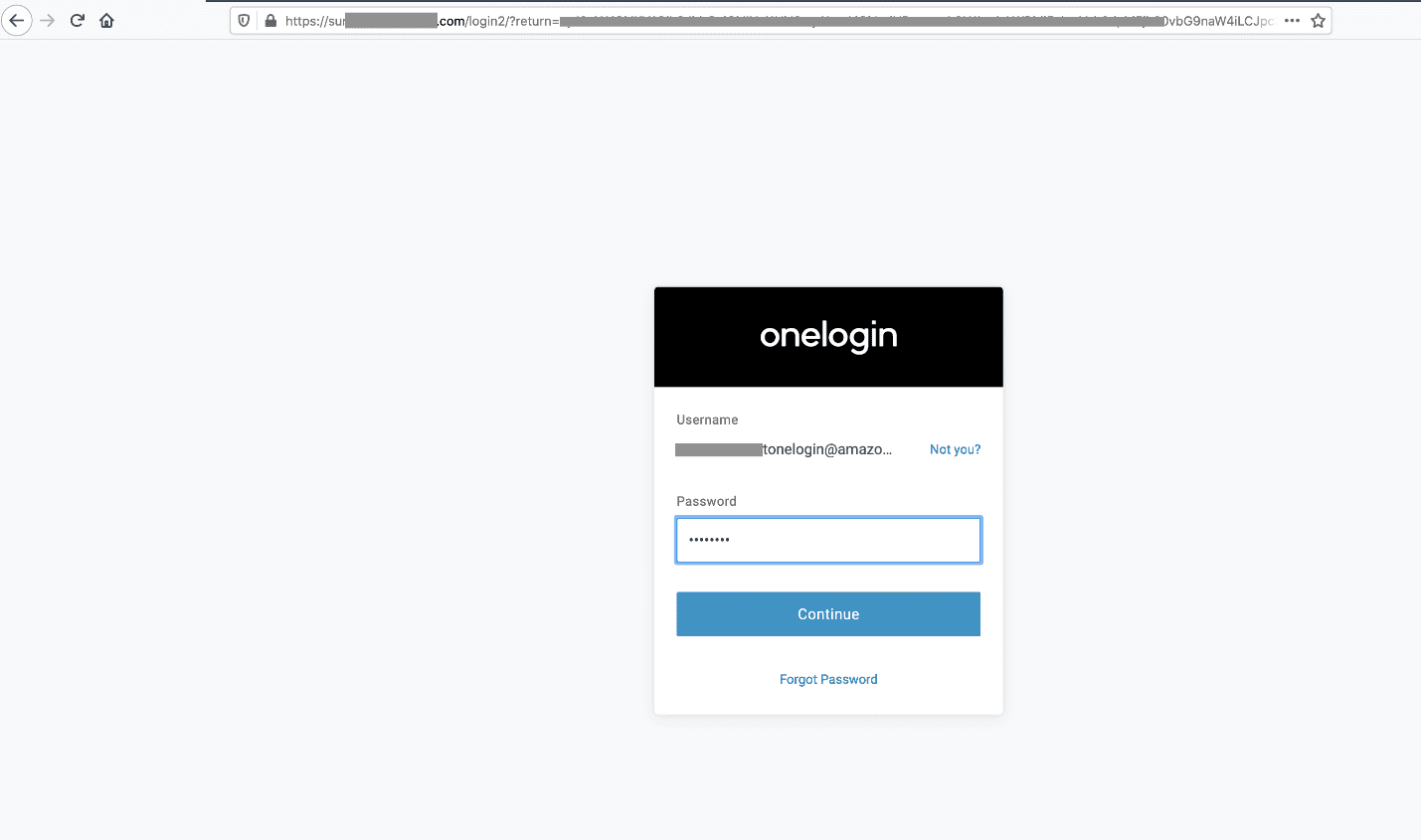
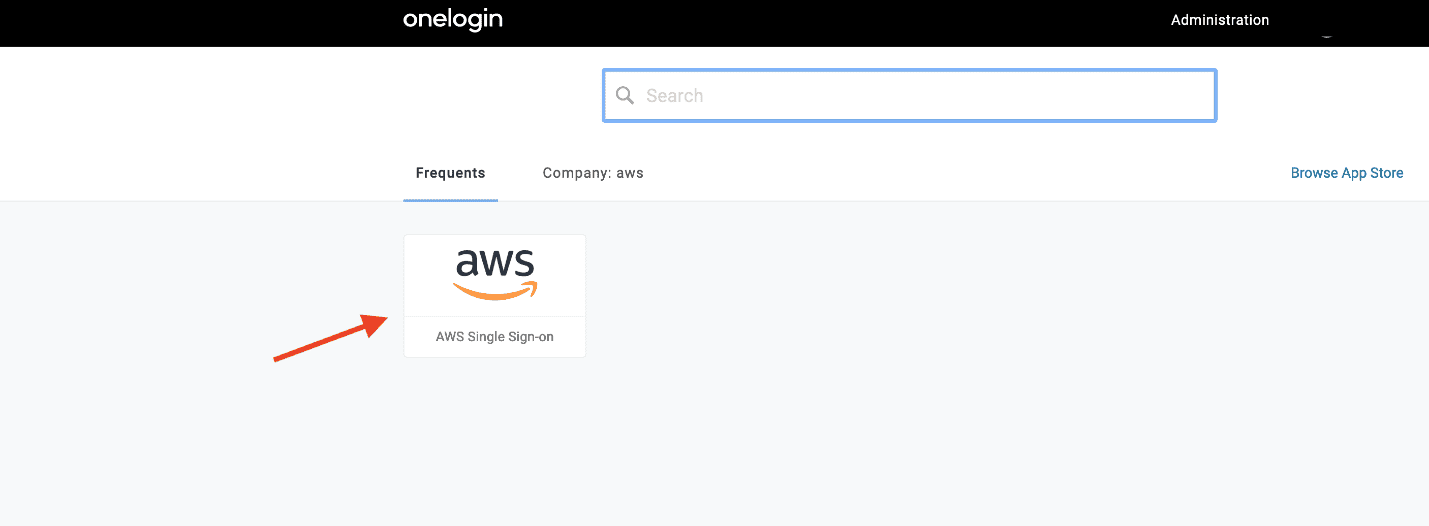
- Sign in to the OneLogin user portal.

- Choose the AWS SSO app.

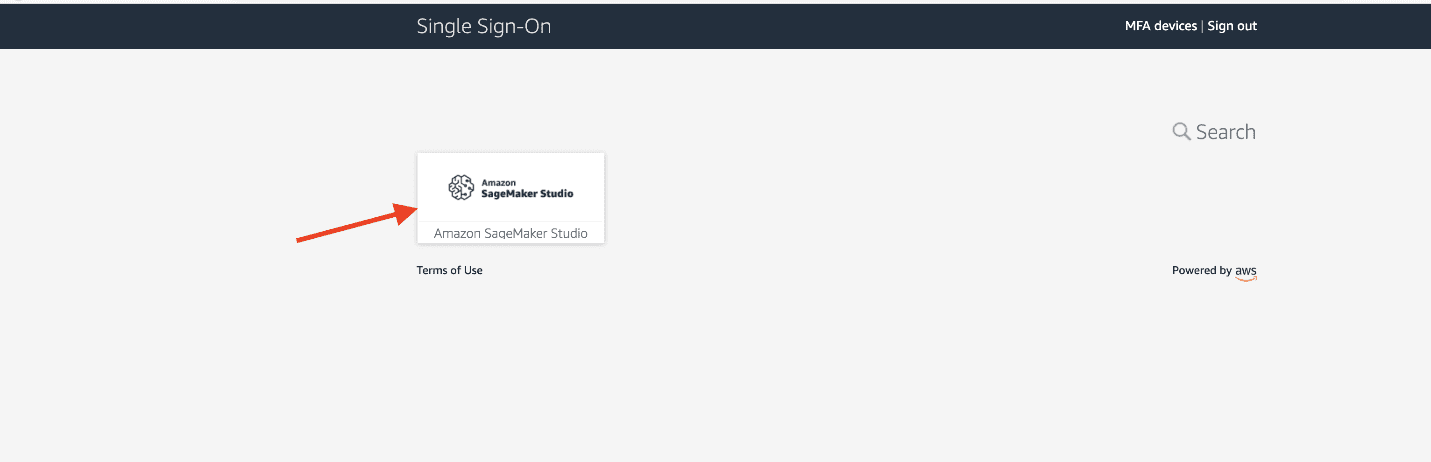
- Choose the tile which says Amazon SageMaker Studio to seamlessly log into your Amazon SageMaker Studio environment.

You’re logged in directly to your user profile inside Amazon SageMaker Studio.
You can also verify the user profiles in Amazon SageMaker Studio directly using the AWS Command Line Interface (AWS CLI):
Conclusion
In this post, we walked through the steps to onboard existing OneLogin SSO users to Amazon SageMaker Studio. We also looked at a reference architecture and how to verify the setup. For more information about using AWS SSO with Amazon SageMaker Studio, see Onboard to Amazon SageMaker Studio Using AWS SSO.
About the Author
 Sam Palani is an AI/ML Specialist Solutions Architect at AWS. He enjoys working with customers to help them architect machine learning solutions at scale. When not helping customers, he enjoys reading and exploring the outdoors.
Sam Palani is an AI/ML Specialist Solutions Architect at AWS. He enjoys working with customers to help them architect machine learning solutions at scale. When not helping customers, he enjoys reading and exploring the outdoors.
 Sunil Ramachandra is a Senior Technical Account Manager at AWS. As a principal technical advisor and ‘voice of the customer’ he helps organizations ranging from start-ups to Fortune 500 enterprises to innovate and operate their workloads on AWS. Sunil is passionate about building AWS integrations that enable Independent Software Vendors (ISVs).When not helping customers, Sunil enjoys spending time with his family, running, meditating and watching movies or originals on Prime Video.
Sunil Ramachandra is a Senior Technical Account Manager at AWS. As a principal technical advisor and ‘voice of the customer’ he helps organizations ranging from start-ups to Fortune 500 enterprises to innovate and operate their workloads on AWS. Sunil is passionate about building AWS integrations that enable Independent Software Vendors (ISVs).When not helping customers, Sunil enjoys spending time with his family, running, meditating and watching movies or originals on Prime Video.
Tags: Archive



Leave a Reply